Your phone buzzes – is it a legitimate alert or another trick? These days, distinguishing real from fake messages is tougher than ever. These deceptive communications, ranging from malicious scams designed to steal data or money to simply unwanted spam, are increasingly sophisticated. While some are merely annoying, others pose significant threats to your personal information and financial security.
This blog will explore different types of fake messages, providing clear examples for each, and equipping you with the knowledge to identify and protect yourself from common digital deceptions.
Red Flags: Common Characteristics of Fake Messages
Before delving into specific categories, understanding the universal warning signs of fake messages is your first line of defense. While sophisticated scams can be convincing, they often contain subtle (or not-so-subtle) red flags that give them away. Train your eye to spot these common characteristics:
- Urgency and Pressure: Fake messages frequently demand immediate action. Phrases like "pay within 12 hours," "final reminder before penalties," or "account will be suspended now" are designed to make you act without thinking or verifying.
- Suspicious Links or Attachments: Always be wary of unfamiliar URLs. These links might contain typos, unusual domains (like .top or strange country codes), or appear shortened. Attachments from unknown senders are also a huge red flag and should never be opened.
- Requests for Personal Information: Legitimate organizations rarely ask for sensitive personal information like passwords, PINs, Social Security Numbers (SSN), credit card details, or bank account numbers directly via text or an unsolicited email.
- Poor Grammar, Spelling, or Formatting: Many fake message examples originate from overseas or are poorly translated. Noticeable typos, grammatical errors, awkward phrasing, or inconsistent formatting (e.g., strange fonts, misaligned logos) are strong indicators of a scam.
- Unusual Sender Information: Check the sender's ID. Is it a generic phone number when it should be a shortcode? Is it an email address from a public domain (like Gmail) when it should be from a corporate domain? Or does the email address itself look nonsensical, like job19991204@sweetbusiness.com?
- Threats or Unbelievable Offers: Messages threatening legal action, prosecution, service disconnection, or promising prizes, lottery winnings, or unexpected inheritance that seem too good to be true are almost always fake.
Type 1: Impersonation & Phishing Scams
One of the most pervasive and dangerous categories of fake messages involves impersonation and phishing. Especially in the US. These SMS scams in the US aim to trick you into revealing personal information or performing actions (like sending money) by pretending to be someone you trust.
Executive/Gift Card Scams (e.g., CEO Impersonation)
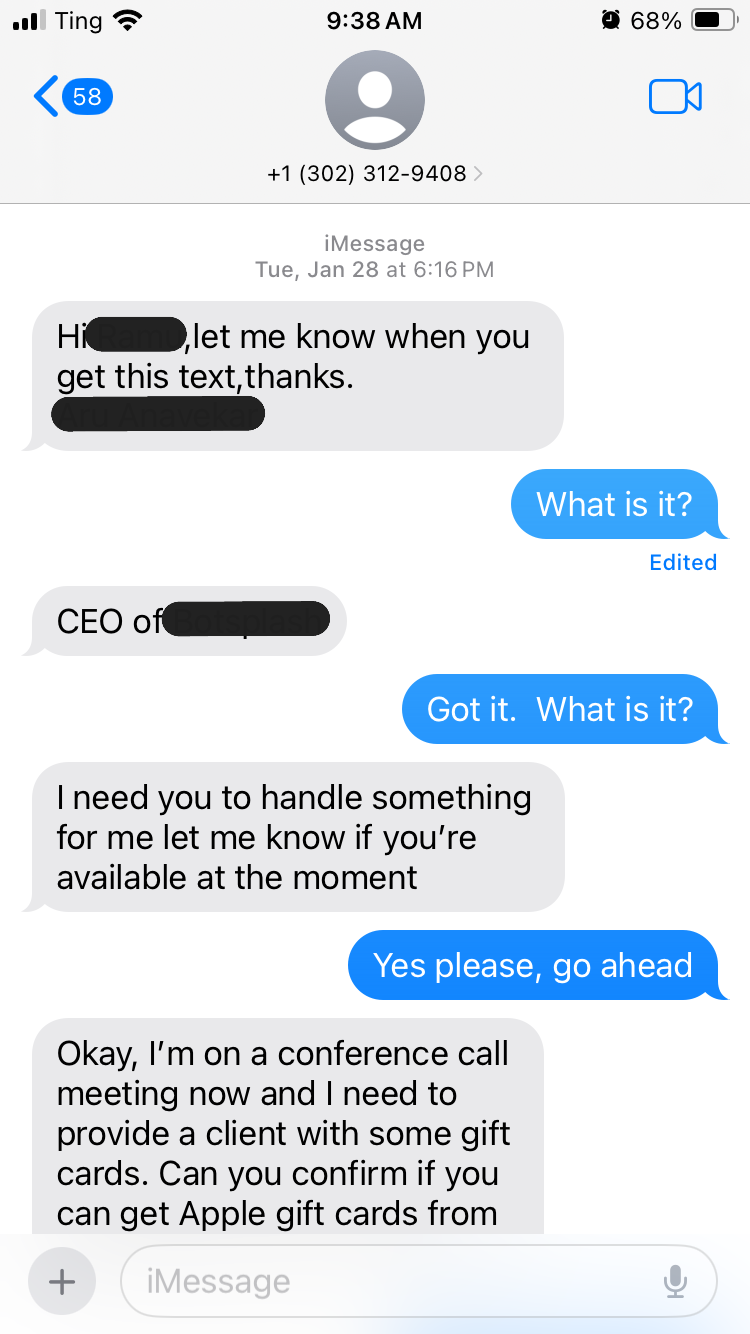
In this common scam, criminals impersonate a high-ranking individual within an organization (like a CEO, manager, or even a team leader) to manipulate an employee or associate. They often create a sense of urgency and confidentiality, asking the victim to purchase gift cards, transfer funds, or share sensitive information, often claiming they are busy in a meeting and cannot do it themselves. The goal is direct financial gain.
The image clearly shows this type of tactic:
"Hi <Name>, let me know when you get this text, thanks. <Sender Name> [claiming to be] CEO of <Company of Recipient>.. ...I need you to handle something for me. Let me know if you're available at the moment... Okay, I'm on a conference call meeting now and I need to provide a client with some gift cards. Can you confirm if you can get Apple gift cards from..."
Red Flags: An unexpected request for gift cards or unusual payment methods (especially from a superior), claims of urgency or being unreachable by phone, grammatical errors, and a sender's number not matching official company contacts.
Government/Utility Impersonation Scams
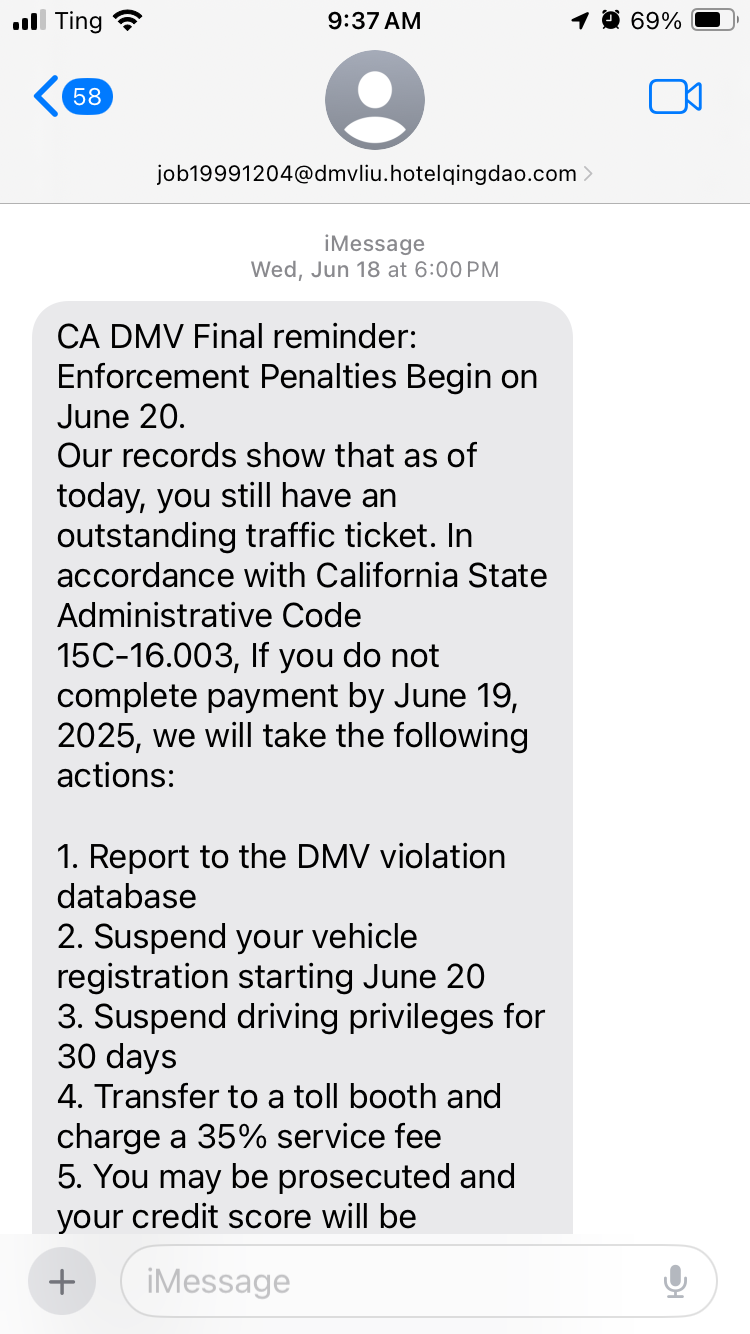
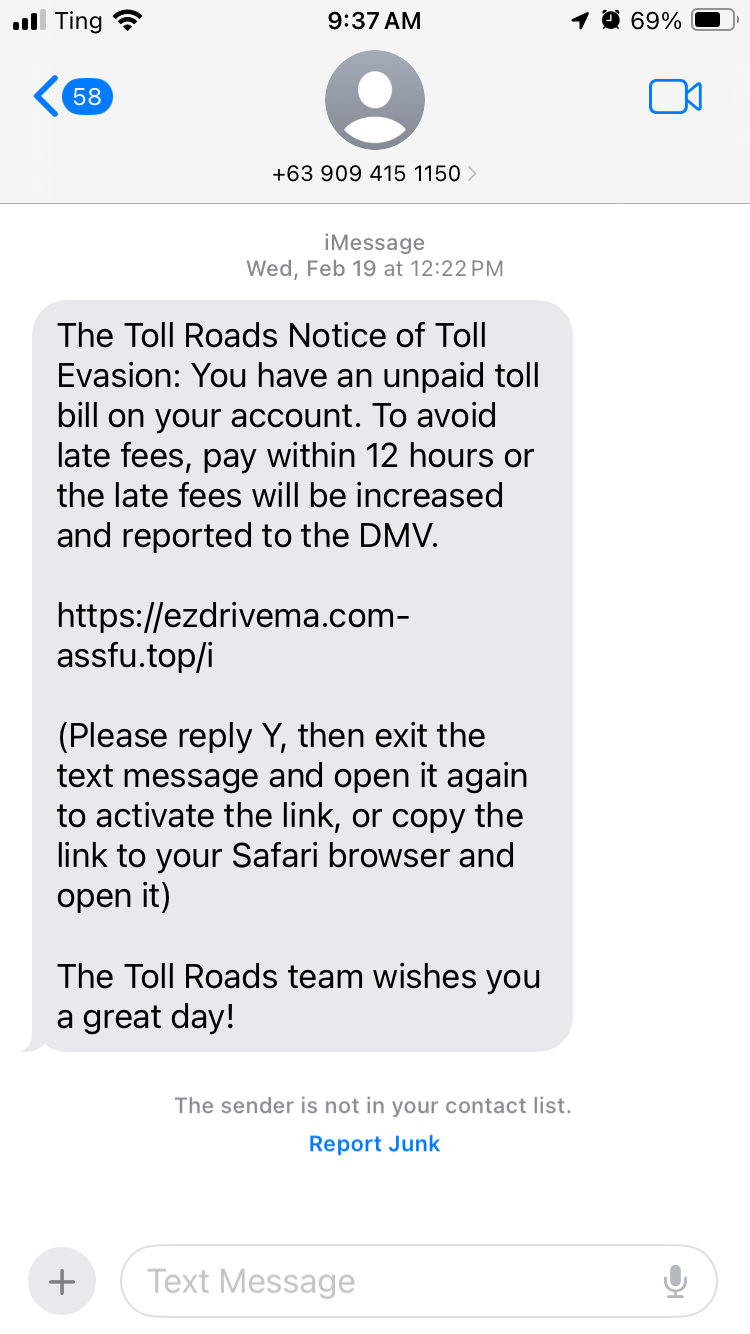
Scammers pose as official government agencies (like the DMV, IRS, police), popular utility companies, or even reputable financial institutions. They typically threaten immediate consequences like fines, arrests, service disconnections, or legal action if an overdue bill isn't paid or a supposed issue isn't resolved promptly. Their primary aim is to scare victims into clicking malicious links or sending money.
The first image provides a classic fake message example of a DMV scam:
"CA DMV Final reminder: Enforcement Penalties Begin on June 20. Our records show that as of today, you still have an outstanding traffic ticket. In accordance with California State Administrative Code 15C-16.003, If you do not complete payment by June 19, 2025, we will take the following actions: 1. Report to the DMV violation database 2. Suspend your vehicle registration starting June 20 3. Suspend driving privileges for 30 days..."
Another clear fake message example from the second image shows a toll evasion scam:
"The Toll Roads Notice of Toll Evasion: You have an unpaid toll bill on your account. To avoid late fees, pay within 12 hours or the late fees will be increased and reported to the DMV. <suspicious link in sms> (Please reply Y, then exit the text message and open it again to activate the link, or copy the link to your Safari browser and open it)."
Red Flags: Extreme urgency and threats of severe penalties, demands for immediate payment, suspicious or unusual links, phone numbers that don't match official sources, and sender details that look unofficial
Type 2: Unsolicited Commercial & Spam Messages
Not all fake messages are malicious scams designed to steal your identity or money. Another common category includes unsolicited commercial messages and general spam. While often less dangerous, they are certainly unwelcome interruptions designed to promote something or gather information without your consent.
Real Estate Solicitations
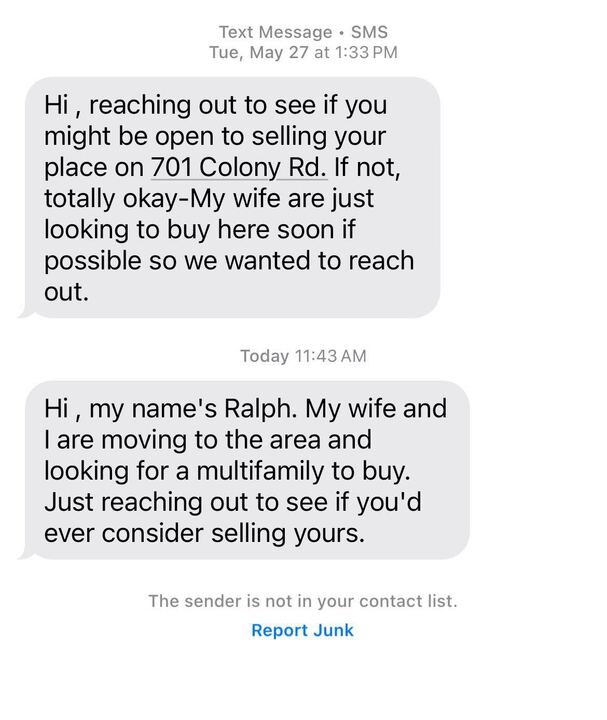
This type of message often comes from real estate agents, investors, or individuals claiming to be looking for property in your area. They send unsolicited texts to inquire about buying your home, land, or commercial property, even if you haven't listed it for sale. These are typically part of a mass outreach campaign.
The image provides a clear fake message example of this:
"Hi , reaching out to see if you might be open to selling your place on 701 Colony Rd. If not, totally okay-My wife are just looking to buy here soon if possible so we wanted to reach out." A follow-up message from the same number states, "Hi , my name's Ralph. My wife and I are moving to the area and looking for a multifamily to buy. Just reaching out to see if you'd ever consider selling yours."
Red Flags: Generic or missing recipient name (e.g., "Hi ,"), unsolicited offers for property you haven't listed, often slightly informal or overly friendly tone for a business inquiry, sender not in your contact list, or a message that seems to be part of a bulk send.
Other Spam Types
This category also includes a wide array of other unsolicited messages that aren't necessarily phishing attempts but are still unwanted. These can range from:
- Unwanted Promotions: Advertising for products or services you didn't opt into.
- Lottery or Prize Scams: Messages claiming you've won a large sum of money or a prize, but require a small "fee" to claim it (which is a transition towards a phishing/money scam).
- Loan Offers: Unsolicited offers for quick loans with too-good-to-be-true terms.
- Political Messages: Texts from political campaigns you haven't subscribed to. The primary intent here is often marketing or lead generation, but without consent, they're considered spam.
Type 3: Technical Support & Malware Scams
Another deceptive category of fake messages preys on your concern for your device's security or your online accounts. These are technical support and malware scams, designed to trick you into compromising your computer, phone, or login credentials.
These messages often claim to be from well-known technology companies (like Microsoft, Apple, Google), your internet service provider (ISP), or even your bank. They send alarming alerts stating that there's a critical problem with your account, device (e.g., a virus detected), or that suspicious activity has occurred. The message then urges you to take immediate action, typically by clicking a provided link or calling a specific phone number, to "fix" the supposed issue.
A common fake message example of this type would be:
"Urgent: Your Apple ID has been suspended due to unusual activity. Click here to verify your account immediately: [malicious link]" or "Security Alert! A virus has been detected on your device. Call Microsoft Support at [fake phone number] now to prevent data loss."
Red Flags:
Unexpected Alerts: Receiving a security alert or problem notification out of the blue, especially if you haven't been interacting with that service.
Urgent Call to Action: Phrases like "Act now!", "Your account will be terminated!", or "Immediate action required" to bypass your critical thinking.
Suspicious Links or Phone Numbers: The links provided in the message are often shortened, have unusual domains, or redirect to phishing websites designed to steal your login credentials or install malware. Phone numbers may connect you to scammers posing as tech support.
Requests to Download Software: Being asked to download remote access software or any unverified application.
Generic Warnings: The message might be vague about the "unusual activity" or "virus" details, hoping you'll panic.
These scams aim to either gain remote access to your device, install malicious software (malware), or steal your account credentials, giving scammers control over your digital life.
What to Do If You Receive a Fake Message
Identifying a fake message is the first crucial step; knowing how to react is the next. Your response (or lack thereof) can be the difference between falling victim and protecting yourself. Follow these guidelines if you suspect a message is fake:
- Do NOT Reply or Click Links: This is paramount. Replying to a suspicious message confirms that your phone number is active and that you're a potential target, inviting more spam or scam attempts. Clicking on any link in a suspicious message can lead to phishing sites designed to steal your credentials, download malware onto your device, or expose your personal information. Even if it asks you to "reply Y" to activate something, do not engage.
- Do NOT Provide Personal Information: Never, under any circumstances, give out sensitive personal information like passwords, PINs, Social Security Numbers (SSN), bank account details, credit card numbers, or any other private data via text message or through an unsolicited link. Legitimate organizations will never ask for this information in such a manner.
- Verify Independently: If a message claims to be from a known entity (your bank, a government agency, a utility company), do not use the contact information provided in the message itself. Instead, independently verify the claim by contacting the organization directly using their official phone number (found on their official website or a trusted bill) or by logging into your account through their official website.
- Report the Message:
- To Your Mobile Carrier: Forward suspicious text messages to 7726 (SPAM). This number works for major mobile carriers in the U.S. and helps them block similar messages.
- To the Federal Trade Commission (FTC): Report phishing and scam attempts at ReportFraud.ftc.gov.
- To the FBI: If you've been a victim of a scam, report it to the FBI's Internet Crime Complaint Center (IC3.gov).
- Block the Number: After reporting, block the sender's phone number to prevent them from sending you future messages. While scammers often use rotating numbers, blocking helps reduce immediate harassment.
Protecting Yourself & Your Data
While knowing how to react to a fake message example is crucial, prevention is always the best defense. Adopting strong digital hygiene habits can significantly reduce your vulnerability to various types of online deception.
- Enable Two-Factor Authentication (2FA) / Multi-Factor Authentication (MFA): This is one of the most effective security measures. Even if a scammer manages to get your password through a phishing attempt, 2FA/MFA requires a second verification step (like a code sent to your phone or a fingerprint scan) to log in, making your accounts much harder to compromise. Enable it on all your online accounts where available.
- Use Strong, Unique Passwords: Never reuse passwords across different accounts. Create long, complex passwords or passphrases that combine uppercase and lowercase letters, numbers, and symbols. Consider using a reputable password manager to keep track of them securely.
- Be Skeptical of All Unsolicited Messages: Cultivate a habit of skepticism. If a message comes out of the blue, even if it looks legitimate, treat it with caution. This applies whether it's an email, a text, or a social media direct message. Always verify the sender and the content through official channels.
- Keep Your Software and Operating Systems Updated: Software updates often include critical security patches that protect against newly discovered vulnerabilities. Enable automatic updates for your operating system, web browser, and all applications.
- Educate Yourself and Your Family: Scammers constantly evolve their tactics. Stay informed about common scam techniques by following cybersecurity news, government consumer protection agencies, and reputable tech blogs. Share this knowledge with your family members, especially children and the elderly, who may be more susceptible.
By consistently applying these protective measures, you build a robust shield against the ever-present threat of fake messages and other forms of digital fraud, safeguarding your personal information and financial well-being.
Conclusion
The increasing sophistication of these tactics demands constant vigilance and a healthy dose of skepticism. By adhering to best practices—never clicking suspicious links, independently verifying unexpected requests, and diligently reporting and blocking dubious senders—you equip yourself with powerful tools against digital deception. In this age of pervasive connectivity, your awareness and proactive security habits are truly your strongest shield against online fraud. Stay informed, stay safe, and protect your digital self.
To learn more about Botsplash click the button below to schedule a demo with our team.

.gif)








